A recent report has raised alarms about the vulnerability of millions of vehicles to a hacking device known as Flipper Zero. Security experts warn that this affordable, handheld gadget can intercept and clone signals from car key fobs, potentially allowing thieves to unlock and steal vehicles with ease. The story has sparked widespread concern among car owners, manufacturers, and cybersecurity professionals.
Background
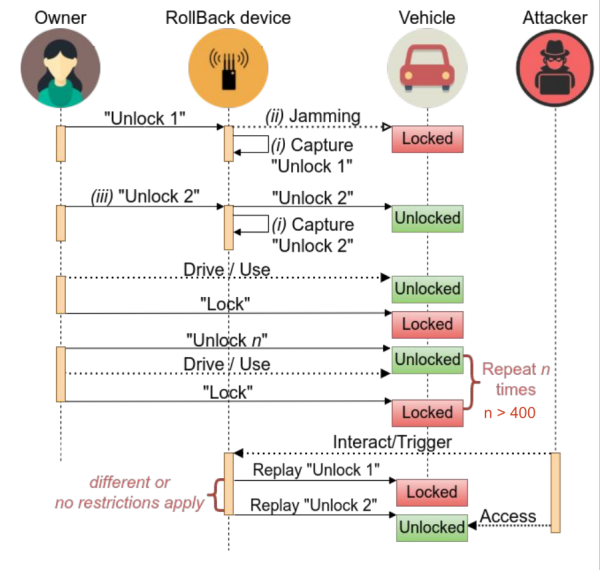
The Flipper Zero device, originally designed for ethical hacking and educational purposes, has gained notoriety for its ability to exploit weaknesses in wireless communication protocols used by many modern vehicles. According to experts, the device can capture radio signals emitted by key fobs and replay them to unlock cars without physical access to the keys. The vulnerability affects a broad range of makes and models, particularly those that rely on older or less secure encryption standards. The manufacturer of Flipper Zero maintains that the device is intended for legitimate security research, but its misuse has prompted calls for regulatory action.
— SecQuest Car Hacking White Paper
Industry Response
Automotive industry representatives have acknowledged the issue, stating that efforts are underway to improve encryption and implement rolling codes that make signal interception more difficult. Cybersecurity experts emphasize the need for consumer awareness and recommend practical steps such as storing key fobs in signal-blocking pouches. Law enforcement agencies have also weighed in, warning that organized crime groups may exploit these weaknesses for large-scale car theft operations.
— Automotive Industry Spokesperson
Public & Expert Views
Public reaction has been swift, with many car owners expressing anxiety over the safety of their vehicles. On Reddit, users debated the responsibility of manufacturers to address these vulnerabilities, with some blaming automakers for failing to update security protocols and others criticizing the availability of hacking tools. Recent social media reports highlight the emergence of custom Flipper Zero firmware sold by hackers that can bypass modern key fob security protections, including rolling codes. This firmware reportedly allows cloning of all key fob buttons by capturing a single command, raising new concerns about the effectiveness of current automotive security measures.
— Mikael Thalen, Journalist (X/Twitter)
Conclusion
The Flipper Zero key fob hack highlights the evolving nature of cybersecurity threats in the automotive industry. While manufacturers are taking steps to address vulnerabilities, consumers are urged to remain vigilant and adopt protective measures. The story underscores the importance of ongoing research, public awareness, and cross-sector cooperation to safeguard vehicles against emerging risks.
Sources Referenced
- Millions of Cars at Risk from Flipper Zero Key Fob Hack, Experts Warn – SAN – July 2025
- Flipper Zero: The Hacker’s Swiss Army Knife or a Toy? – arXiv – October 2022
- Mikael Thalen (@MikaelThalen) – X post on custom Flipper Zero firmware bypassing rolling codes
- SecQuest – Car Hacking White Paper
Image Credit
Featured image: Flipper Zero device and car key fob by SecQuest (SecQuest).

Join the Discussion